2025 Cybersecurity Guidebook Chapter 1: Protecting logins
We are kicking off CGP’s 2025 Cybersecurity Guidebook a few months early. This series provides a deep dive into the various ways you should be protecting your small business, starting with secure logins, and moving through various other technologies such as backups and insurance. This guidebook is intended to be insightful and actionable for small businesses looking to protect themselves, and emphasizes low/no-cost options.
—————
Chapter 1: Protecting logins
Why? A login is a username (often an email address) plus other factors of authentication such as the traditional password, multifactor prompt, or passkeys. Logins protect access to a system, and are one of the most frequently exploited systems these days. This is because you and your IT/security team no longer have control of many systems due to third party vendors and the cloud. With that in mind, what can we do to better protect ourselves?
Enable any multifactor authentication (MFA) functionality. A 2019 Microsoft study showed MFA would have stopped over 99% of successful Office 365 attacks. Almost every modern software/cloud platform includes MFA, the only argument for not turning it on is that it can be annoying. So is having to unlock your front door, but we rarely hear people complaining.
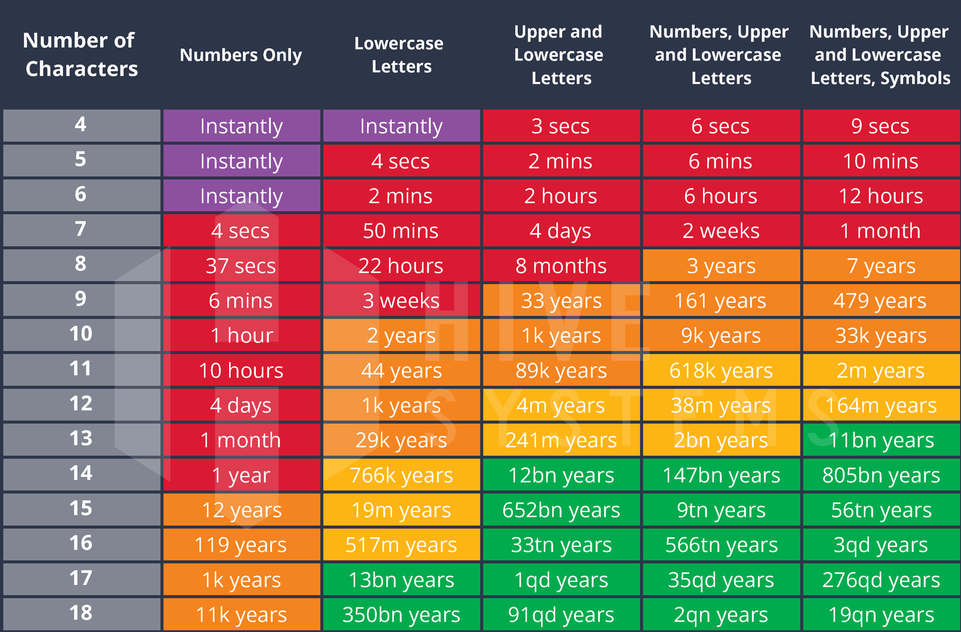
Use a longer (but not necessarily complex) password. Hive Security’s famous password complexity chart (below) shows the value of length versus complexity. Compare the 4m years a 12 character text only password takes to crack versus the 7 years a high complexity 8 character password takes. Leveraging multiple words in a series “texasNetherlandsLondon” is easier to remember AND more secure versus “t3xa$2024”.
Use different passwords for each website and system. Due to the pervasiveness of emails as usernames, hackers will frequently find a login for “trey@gmail.com” and then reuse that email and password combination across other sites.
Password managers allow the use of extremely long passwords, and unique passwords per site, without having to remember which goes to what site. There are plenty of free options (CGP is big fans of Bitwarden which has a free personal use version) and paid options as well. Avoid the built in browser managers if possible, but if you must use them, make sure you have a master password. (Without the master password, the security is extremely weak. These systems are better than no password manager at all, but are not as good as a true standalone password manager.)
Disable old and unused accounts as quickly as possible. One frequent mistake small businesses make is leaving an account active after an employee leaves “in case we need something.” Most modern systems allow you to disable the account and still access it through another user. “In case accounts” are a prime target for hackers since they are intentionally not being maintained. Schedule an annual or quarterly review of active accounts for each system and disable old accounts as soon as possible.