Due Diligence Preparation Part 2: Cybersecurity/IT Resilience
In part 1 of our discussion around due diligence requirements, we discussed how you can build a formal program around your biggest risk - vendors. The other major focus of current due diligence requests is around resilience. In this situation, we are talking about your ability to handle a major outage, disaster, breach or other incident. Historically, IT has focused on preventing incidents, and has neglected recovery preparation from the incident. Due to the exponential increase in cyberattacks, the focus has shifted to the ability to recover - resilience.
Building cybersecurity & IT resilience
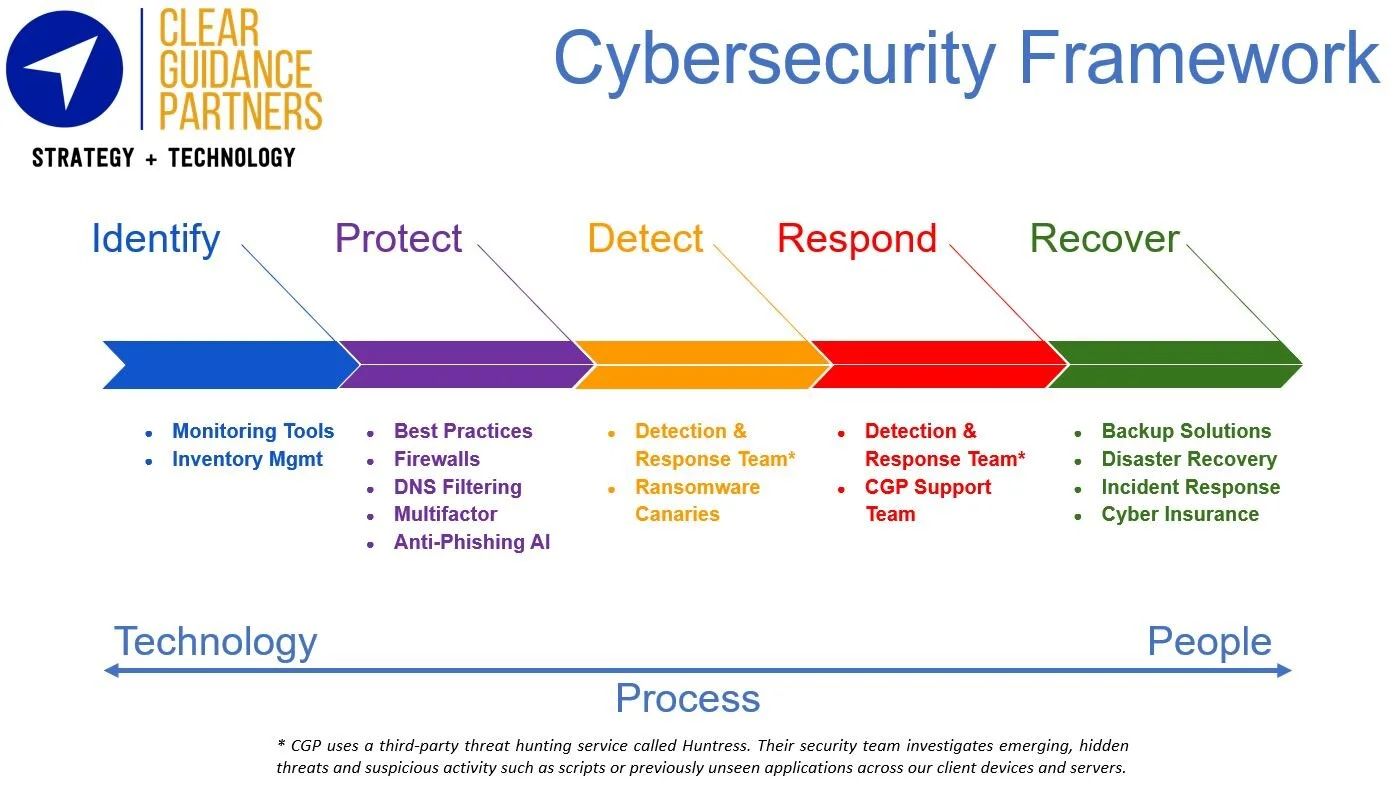
To start, we’ll revisit our favorite security framework recommended by the National Institute of Standards and Technology (NIST CSF). Resilience primarily lives in the final two stages of respond and recover.
There are a few key processes you need in place as a baseline:
Incident response (IR) policy: this consists of key steps to take when a possible incident is identified. Remember that something is better than nothing, even a brief IR plan will help. A few important notes for a solid plan:
If you have ever taken CPR certification, remember that you pick someone specific to call 911. Same thing in your IR plan, each role should be specific as possible on who performs it.
For your technical response team, you should start with your cyberinsurance provider, or have an established relationship. Now is NOT the time to start calling local IT companies who may not be qualified for IR.
Include your insurance policy info, including their claims hotline or email address.
Disaster Recovery (DR) plan: this can be integrated into the IR plan, but specifically applies to bringing key systems back online and/or processes to replace them while unavailable. As always, start with the basics. How will your team communicate? If cell phones for example, where is that list of numbers accessed? Include contact info for key third parties such as your email and accounting providers.
Test processes and perform table top exercises (TTE): a TTE is a great opportunity to talk through how an incident would impact your business. By role playing through a common incident, you can identify gaps in your processes. CISA (a government security agency) provides several excellent templates, or your IT team should be able to provide some. No process is perfect, and due to how rapidly the cybersecurity world changes, you should always be testing and improving your processes.
Ready to bring in the experts? Security is the cornerstone of CGP, with full attention paid to all five phases of the CSF.