Security Breaches: "When, not if"
An important part of modern IT security is “assuming breach” - that your business will have a security incident, it is just a matter of time. The chances of your building catching on fire are very low, but you still have things in place to detect, respond, and recover from a fire like smoke detectors and insurance…right?
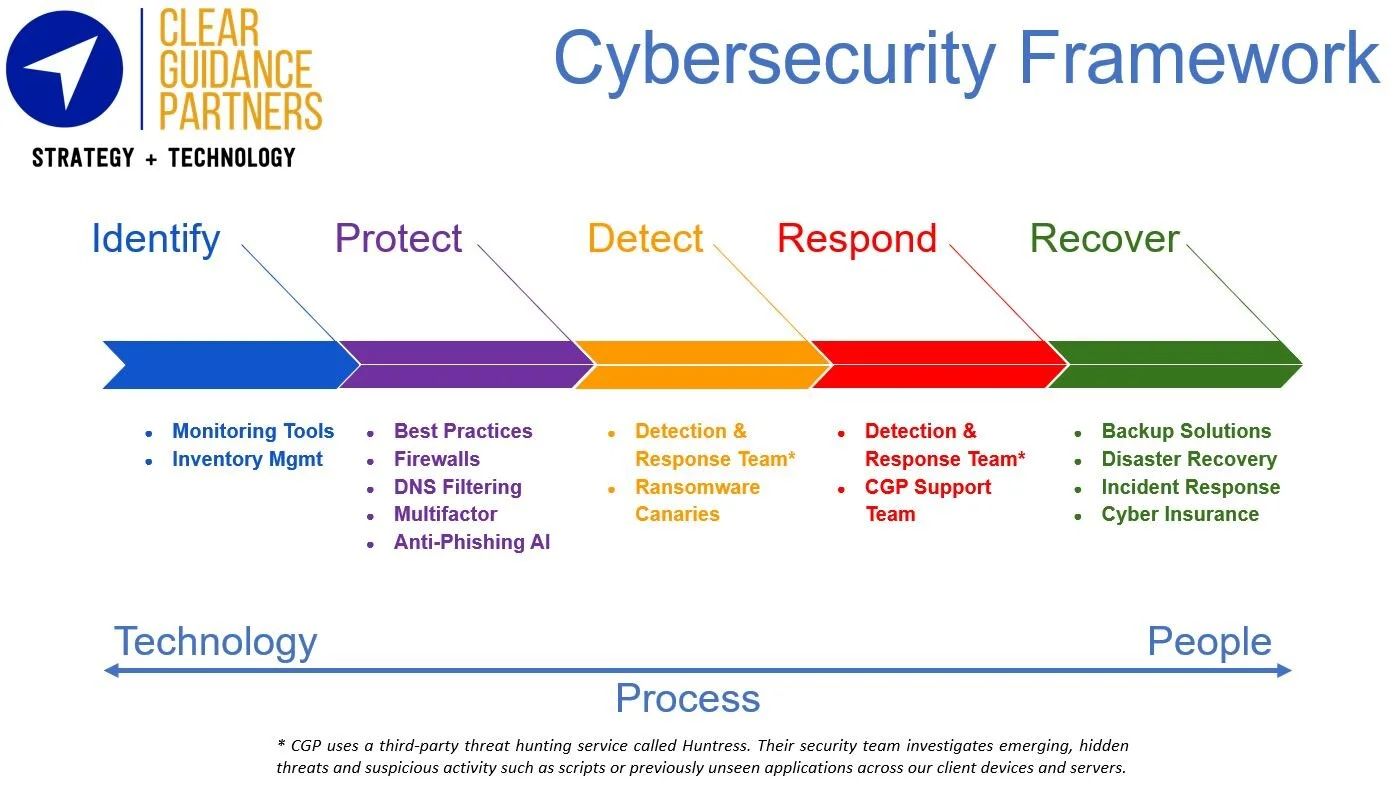
The NIST Cybersecurity Framework divides IT security into five phases, the “boom”, or breach, occurs between Protect and Detect. Traditionally IT has focused 99% of efforts and budget on the first two phases, with some emphasis on Recover. However, the recover aspect was typically due to server failures and needing to restore from backup.
Modern IT requires a relatively equal emphasis on all five phases, but the most critical may be Detect. An incident starts when an attacker gains access to some part of your network. On average a hacker is in a network for 11 days before they are detected, plenty of time to download sensitive data or ransom the entire business.
The next two phases quickly come into play, as you first must secure the network from the attackers, then recover the operations of the business.
When building a modern security plan, there are a couple of easy steps that instantly make a business much more resilient and ready to recover from an attack.
24x7 network surveillance and response: Do hackers work 8x5 shifts? Absolutely not. Even a few hours alone in a network is long enough for them to steal files or deploy ransomware to the entire business. Network surveillance services have become relatively affordable which give you a team watching your business around the clock.
Have an incident response (IR) plan. Start simple, something is better than nothing. Who responds? What will be communicated to clients? How will the team communicate when email and the phone system are completely offline?
A cyberinsurance policy. Most will include a technical team for IR, including advanced forensics. They are usually the first call that should be made. After the breach is contained, cyberinsurance provides extensive recovery services such as business interruption reimbursement, legal services, PR, and more.
Simple security such as multifactor authentication (MFA), resilient backups, and user security training make you less of a target. A lot of hackers are looking for low hanging fruit, so making yourself a harder target encourages them to move on.
At Clear Guidance, security and resilience is built into everything we do. Our sole IT services plan includes a full suite of security, incident response, and disaster recovery. Our CIOs work closely with your executive team to identify and mitigate risks within your business, focusing on both prevention and recovery. Talk to a partner today: